Password authenticated key exchange-based on Kyber for mobile devices
- Published
- Accepted
- Received
- Academic Editor
- Ivan Miguel Pires
- Subject Areas
- Algorithms and Analysis of Algorithms, Cryptography, Security and Privacy
- Keywords
- Post-quantum cryptography, Password-based authenticated key exchange, Lattice-based cryptography
- Copyright
- © 2024 Seyhan et al.
- Licence
- This is an open access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, reproduction and adaptation in any medium and for any purpose provided that it is properly attributed. For attribution, the original author(s), title, publication source (PeerJ Computer Science) and either DOI or URL of the article must be cited.
- Cite this article
- 2024. Password authenticated key exchange-based on Kyber for mobile devices. PeerJ Computer Science 10:e1960 https://doi.org/10.7717/peerj-cs.1960
Abstract
In this article, a password-authenticated key exchange (PAKE) version of the National Institute of Standards and Technology (NIST) post-quantum cryptography (PQC) public-key encryption and key-establishment standard is constructed. We mainly focused on how the PAKE version of PQC standard Kyber with mobile compatibility can be obtained by using simple structured password components. In the design process, the conventional password-based authenticated key exchange (PAK) approach is updated under the module learning with errors (MLWE) assumptions to add password-based authentication. Thanks to the following PAK model, the proposed Kyber.PAKE provides explicit authentication and perfect forward secrecy (PFS). The resistance analysis against the password dictionary attack of Kyber.PAKE is examined by using random oracle model (ROM) assumptions. In the security analysis, the cumulative distribution function (CDF) Zipf (CDF-Zipf) model is also followed to provide realistic security examinations. According to the implementation results, Kyber.PAKE presents better run-time than lattice-based PAKE schemes with similar features, even if it contains complex key encapsulation mechanism (KEM) components. The comparison results show that the proposed PAKE scheme will come to the fore for the future security of mobile environments and other areas.
Introduction
The security of conventional public-key cryptosystems (PKC) changed with the post-quantum concept that emerged with ongoing processes for developing quantum computers and the proposal of the Shor algorithm. The traditional PKCs such as key exchange (KE)/KEM and digital signature schemes will be insecure in the presence of large-scale quantum computers with Shor algorithm (Peikert, 2016). NIST started a process to set the post-quantum secure standard for PKC in 2016 (NIST, 2022a). In 2022, lattice-based Kyber was determined as the standard in the KEM category. For digital signature usage, lattice-based Crystals-Dilithium, Falcon, and hash-based SPHINCS+ were selected as the standard (NIST, 2022b). Although the standards were determined to be ready PQC era, it is still necessary to design and determine cryptosystems that can be used for particular goals and application areas.
One of the PKC primitives used for specific purposes is the PAKE scheme that provide a high-entropy shared key generated using low-entropy password-based authentication. Due to the easy-to-use structure, PAKE schemes do not require special hardware to store high entropy keys (Bellare, Pointcheval & Rogaway, 2000). The hardness assumptions of these schemes are also based on discrete logarithm and factorization problems like other PKCs. The first PAKE, encrypted key exchange, was proposed by Bellovin and Merritt in 1992 (Bellovin & Merritt, 1992) and many PAKE proposals, including new theoretical models, were presented in the following years (Bellovin & Merritt, 1993; Jablon, 1996; Wu, 1998; Hao & Ryan, 2011; Shin & Kobara, 2012). In addition, Internet Engineering Task Force (IETF), The Institute of Electrical and Electronics Engineers (IEEE), and the International Organization for Standardization (ISO)/International Electrotechnical Commission (IEC) conducted studies on the standardization of PAKE protocols (Hao & van Oorschot, 2022). The most recent standardization initiative for PAKE schemes was the process initiated by the IETF in 2019. In this call, completed in March 2020, OPAQUE and CPace schemes were declared as the PAKE standard for today’s usage (Hao, 2021). Although the industry has started to prototype PAKE protocols in real applications with these processes, the adaptation of post-quantum secure algorithms is necessary for future security.
With the development of wireless communication technologies, the increasing use of mobile devices has brought the security of these devices into focus. There is a need for post-quantum secure PKCs such as KEM, authenticated key exchange, and PAKE that consider resource limitations for mobile devices (Dabra, Bala & Kumari, 2020). Lattice-based cryptosystems stand out with their strong proof of security, worst-case hardness, efficiency, and post-quantum security features. Up-to-date literature shows that there have not been many lattice-based PAKEs for mobile device security. In Dabra, Bala & Kumari (2020), an anonymous ring learning with errors (RLWE)-based two-party PAKE was designed for the post-quantum security of the mobile environment. The security analysis of this scheme, which includes a four-phase approach, was done by considering real-or-random (RoR) assumptions. An improved version of Dabra, Bala & Kumari (2020) with a practical randomized KE approach is proposed in Ding, Cheng & Qin (2022) to capture signal leakage attack resistance. In Islam & Basu (2021), a four-phase RLWE-based PAKE was constructed for two mobile devices-one server communication model. The security-related examinations were done by following ROM definitions. In Seyhan & Akleylek (2024), we also built a four-phase PAKE to achieve reusable key and anonymity features for mobile device-server communication model. In the security analysis, we followed RoR assumptions to prove the semantic security. According to the up-to-date studies, many other PAKEs with lattice primitives such as Ding et al. (2017), Gao et al. (2017), Liu et al. (2019), Seyhan & Akleylek (2023) and Ren, Gu & Wang (2023) were designed using traditional PAK model to capture explicit authentication and PFS. The provided proposals can be suitable for post-quantum key agreement requirements, but none of them has been focused on the PAKE version of the NIST standard. We know that the security of Kyber has been deeply studied and it was designed with efficient structures. Therefore, proposing a PAKE version of this algorithm and providing reference implementations will come to the fore in post-quantum secure PAKE literature.
Motivation and contribution
PAKE protocols are commonly used for credential recovery, wireless fidelity communication, device pairing, end-to-end (E2E) secure channel applications, and Kerberos-like usage areas as a part of secure communication in daily life. It is known that ensuring today’s and post-quantum security of PAKE schemes is one of the main open problem regarding security in the future (Ott & Peikert, 2019; Hao & van Oorschot, 2022). Although the strongest candidates can be built with NIST algorithms, PAKE versions of these schemes have not been constructed yet. To propose a solution for this open problem, we used well-defined Kyber KEM structures to construct password-based authentication. We mainly aimed to solve the post-quantum authenticated key-sharing requirement of traditional computing power and mobile devices by providing a PAKE version of the PQC standard Kyber scheme. The contributions of Kyber.PAKE proposal to the literature are listed as follows.
-
A novel two-party Kyber.PAKE is constructed to meet the post-quantum secure PAKE requirement for general purposes and mobile networks based on NIST PQC KEM standard. The conventional PAK design suite (MacKenzie, 2002) is adapted to MLWE problem since the main security of Kyber is based on MLWE.
-
KEM structures and MLWE-based PAK design idea are used simultaneously to construct the PAKE version of Kyber. So, the proposed Kyber.PAKE provides explicit authentication and PFS without using a trusted third party, public key infrastructure, and signature.
-
The security of Kyber.PAKE is deeply analyzed by making some assumptions about whether an adversary can obtain the shared key with an online dictionary attack or not. In the analysis, the advantage of the adversary is shown to be negligible in the ROM by following the Bellare-Pointcheval-Rogaway (BPR) (Bellare, Pointcheval & Rogaway, 2000) and CDF-Zip models (Wang et al., 2017). Since CDF-Zipf characterizes password distribution, theoretical security analysis is performed by better covering the real-world power of the adversary.
-
The implementation of the Kyber.PAKE is written in C (Dursun, 2023a) and Java (Dursun, 2023b). The experimental results are presented in terms of cost, central process unit (CPU) cycle, and run-time. Based on Java implementation, the mobile device performance are also provided by considering running time, energy, memory, and CPU usages.
-
Reference results show that the proposed Kyber.PAKE is one of the best choices to meet authenticated key generation requirement of post-quantum era with the usage of simple structure PAKE design and KEM with strong security.
Outline
In ‘Preliminaries’, the mathematical background is summarized. In ‘Proposed Kyber.PAKE Scheme’, the general working steps and correctness of the constructed Kyber.PAKE are defined. In ‘Security Analysis’, the detailed security examinations against dictionary attacks is presented. The implementation results and comparison with current literature are provided in ‘Reference Implementation and Comparison Results’. In the last part, ‘Conclusion and Future Directions’, the future directions and conclusion are figured out.
Preliminaries
The notation is provided in Table 1.
| ℤq: Integers in modulo q. | Rk: k-dimensional vector of polynomials (R). |
| mod+: Let α ∈ ℤ+. a′ = amod+α|a′ ∈ [0, …, α). | : Rkinmodq |
| ||: Concatenation operator. | κ: Security parameter. |
| Bℓ - B∗: Byte array of length ℓ and arbitrary, respectively. | : MLWE distribution. |
| : The correctness distribution of Kyber. | Bη: CBD of Kyber. Let η ∈ ℤ+. For , a Bη sample is obtained with . |
| : Bη distribution over Rk. | dt, dv, du: Reconciliation parameters of Kyber. |
| pwC: Client’s password. | a←rχ: a is randomly chosen from the distribution χ. |
| sid - cid: Server id - Client id. C - S - V: Client - Server - Participant Spaces. | . |
| ϵ: A negligible value in κ. | H2(⋅) = SHA3 − 256:{0, 1}∗ → {0, 1}k. |
| U(⋅): Uniform distribution. | mod±: Modular reduction. Let α ∈ 2ℤ+.a′ = amod±α|a′ ∈ (−α/2, …, α/2]. |
| H3(⋅) = SHA3 − 256:{0, 1}∗ → {0, 1}k Key derivation function (KDF) is used to obtain k-bit session key. | pk - sk: Public key - Secret key. |
| negl(κ): Let ϖ > 0 and κ > n0. If an n0 ∈ ℕ can be found such that negl(κ) < κ−ϖ, negl is determined as a negligible function. | |
| Dpk: pk distribution of Kyber KEM defined with B12kn/8+32. | Dct: ct distribution of Kyber KEM defined with Bdukn/8+dvn/8. |
| CCA: Chosen-ciphertext attack. | XOF: Extendable Output Function |
| NTT: Number-Theoretic Transform. | CPA: Chosen-plaintext attack. |
| NTT−1: Inverse NTT. | PKE: Public Key Encryption. |
| PFR: Pseudo-random function. | Adv: Advantage |
| A: Adversary | CBD: Centered Binomial Distribution. |
| ssk - ct: Shared secret key - Ciphertext. | S: Abbreviation of Kyber.PAKE. |
Basic definitions
In the proposed PAKE, the shared key is obtained by using Kyber PKE and KEM functions/components and the password-based authentication is added by following PAK design idea.
Kyber PKE and KEM functions are recalled in Table 2. To obtain detailed information, we refer to Avanzi et al. (2019).
In Table 2, KYBER.CCAKEM uses KYBER.CPAPKE functions to obtain key agreements based on the MLWE problem. Since the main security of Kyber and the proposed PAKE version are based on the hardnesses of MLWE, the key generation is done by following the MLWE assumption.
Definition 1 (MLWE (Bos et al., 2018)) Let k ∈ ℤ+, , , and ei←rbη. MLWE distribution is obtained as follow.
The hardness of MLWE is defined by decisional-MLWE (d-MLWE). Let m independent (ai, bi) instances are given (). d-MLWE is a problem that decides whether these samples belong to MLWE (, where and ) or uniform distribution ().
Let A be an adversary. The advantage (Adv) of A to solve d-MLWE problem is determined by
In Table 2, the computations of pk and ct are done by discarding low-order bits that don’t affect the accuracy of decryption to achieve reconciliation and reduced parameters. The reconciliation functions of Kyber are recalled in Definition 2 (Bos et al., 2018).
Definition 2 (Compress and Decompress Functions (Bos et al., 2018)) Let a ∈ ℤq and d < ⌈log2(q)⌉.
-
b =Compress q(a, d): For a ∈ ℤq, the output of Compress is defined by .
-
b′ =Decompress q(b, d): For b ∈ {0, …, 2d − 1}, the output of Decompress is determined by , where b′ is an element which is relatively close to b.
The distribution |b′ − bmod±q| ≤B q = ⌈q/(2d+1)⌋ is nearly uniform over the integers of maximum magnitude Bq. Note that Definition 2 is defined over ℤq. In Kyber, since , for each coefficient of a is evaluated under these functions.
In Kyber (Bos et al., 2018), the reconciliation is provided by using the Compress and Decompress functions. So, is defined to satisfy the correctness. The output of distribution is generated in the following way.
-
A y←rRk is chosen.
-
return (y −Decompress q((Compressq(y, d)), d)) mod±q.
Although the main operations of Kyber are performed in the NTT domain, all polynomials are sent in the normal domain. For the transformation of polynomials to be used in the protocol flow, encode and decode operations are done (Bos et al., 2018; Avanzi et al., 2019).
Definition 3 (Decodeℓ): Let B32ℓ be a byte array. Then the output of Decodeℓ is defined by f = f0 + f1X + f2X2 + ⋯ + f255X255, where fi ∈ {0, …, 2ℓ − 1}. In other words, it deserializes a 32ℓ bytes array into a polynomial with B32ℓ → Rq.
Note that Encodeℓ is determined as the reverse of Decodeℓ.
The correctness of Kyber.PAKE is analyzed by using the correctness assumptions of KYBER.CCAKEM and KYBER.CPAPKE. The main theorems of these schemes are recalled in Theorems 1 and 2, respectively.
Let k ∈ ℤ+, , e2←bη, , , cv←ψdv, and . Then, KYBER.CPAPKE scheme runs with (1 − δ)correctness probability (Bos et al., 2018).
Let G be a random oracle (RO) and KYBER.CPAPKE is correct with (1 − δ) probability. KYBER.CCAKEM also runs with (1 − δ)correctness probability (Bos et al., 2018).
The security evaluations of Kyber.PAKE is presented based on the ROM assumptions of Kyber.
Definition 4 (ROM Security of Kyber KEM (Avanzi et al., 2019)) Let XOF, H, and G be the ROs, nro be the maximum number of A’s queries to ROs, and B–C be the adversaries who have roughly the same run-time as A. The adventage(Adv) of A over Kyber KEM in the ROM is defined by Eq. (1)
Security model
In this section, special terms and basic primitives of the used security model are detailed.
In the construction of Kyber.PAKE, password-related primitives are added to provide main authentication by adapting traditional PAK (MacKenzie, 2002) design to the MLWE problem. In the analysis, the resistance against password dictionary attacks is investigated with the help of BPR (Bellare, Pointcheval & Rogaway, 2000) definitions.
-
C ∈ C, S ∈ S, V ∈ V = C∪S.
-
DS denotes password space which is constructed according to Zipf’s rule (Wang et al., 2017).
-
Each C has pwC←rDS and related S holds the hash of pwC.
-
A is designed as a probabilistic algorithm, which can control the entire network and provide input for the participant’s instances.
-
By using the RO queries, A can launch the attacks.
-
Let S be a scheme and be ith V instance that can only be used once. A’s special query band is defined as follows.
-
execute(C, i, S, j): S occurs between and . The outputs of executed S are sent to A.
-
send(V, i, M): Message M is sent to . Then, according to S, the computations of the scheme are done by . The outputs are sent to A.
-
reveal(V, i): Let be an accepted and has its own ssk. As a result of this query, ssk is sent to A.
-
corrupt(V): It returns the password of V. If V ∈ C, the output is pwC. Otherwise, H1(pwC).
-
test(V, i): Let b be the coin of . With this query, A tosses b. If b = 0, ssk is sent to A by . Otherwise, ssk is chosen uniformly at random from ssk space and is returned to A.
-
-
p-id and s-id are the id’s of the parties and a session, respectively.
-
ne, ns, nr, nc, and no represent the maximum number of A’s execute, send, reveal, corrupt, and RO queries, respectively.
-
Texp represents the generation time of the MLWE samples.
According to the BPR model, each user can run the scheme multiple times with different partners.
Definition 5 (Instance Partnership (Bellare, Pointcheval & Rogaway, 2000)) Let and have(p-idi, s-idi, sski) and (p-idj, s-idj, sskj), respectively. If the following conditions are satisfied and are considered as partner instances.
-
U ∈ C and V ∈ S, or V ∈ C and U ∈ S.
-
sski = sskj, p-idi =V, and p-idj =U.
-
s-idi =s-idj = s-id, where this value is not null.
-
A third oracle other than and should not have the same s-id.
In the security analysis, the instance freshness provides PFS.
Definition 6 (Instance Freshness (Bellare, Pointcheval & Rogaway, 2000; MacKenzie, 2002)) Let and be partner. If none of the following events occurred, is defined as a fresh instance that provide forward secrecy.
-
A reveal(W, i) query
-
A reveal(V, j) query
-
A corrupt(V) query before send(W, i, M) and test(W, i) queries.
By using definitions and query band, the advantage of A in the PAKE scheme is examined.
Definition 7 (Advantage of an A (Bellare, Pointcheval & Rogaway, 2000; MacKenzie, 2002)) Let be a fresh instance, S be the PAKE scheme, and be an event that A makes a b′ = test(V, i) query. For b that was selected in the test query, if b′ = b, the advantage of A is defined byEq. (2)
If the security analysis show that Eq. (2) is negligible, then the constructed PAKE is said to be secure under the ROM assumptions.
In the traditional PAK suit, the main advantage of the adversary is determined by considering that the password and uniform distribution have the same properties. Since this idea does not cover the real power of the adversary, CDF-Zipf is used to characterize the password distribution.
Definition 8 (CDF-Zipf Model (Wang et al., 2017)) Let DS be the password dictionary size and nop be the maximum number of A’s online password guess attempts. In the traditional approach, the propability of A’s correct password guess is defined by . According to the recent studies (Wang et al., 2017), this evaluation underestimate A’s power in real-world applications since the passwords of users generally follows CDF distribution. So, CDF-Zipf is followed to give more real-world-based results in terms of password distribution.
Let C′ and f be CDF constants. The probability of A’s correct password guess in CDF-Zipf model is determined by (3) Note that CDF constants are determined according to the usage area by using linear regression.
Proposed Kyber.PAKE Scheme
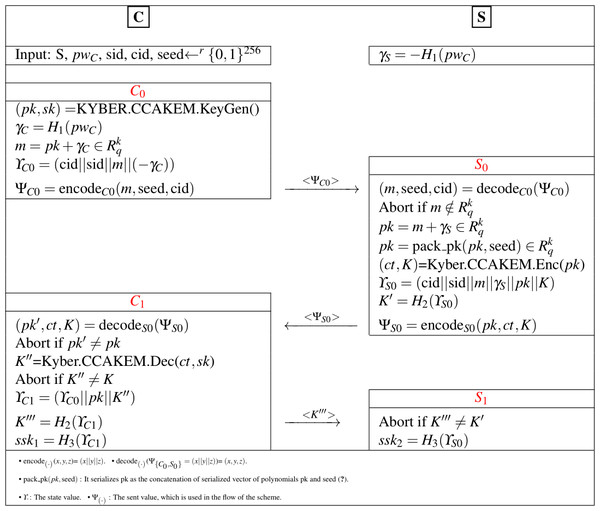
The password-authenticated version of Kyber KEM (Avanzi et al., 2019) is obtained with the combination of KYBER.CCAKEM.KeyGen, KYBER.CCAKEM.Enc, and KYBER.CCAKEM.Dec structures, given in Table 2, and MLWE-based one-phase PAK idea. The proposed Kyber.PAKE runs between client (C) and server (S) and contains four main sub-processes (C0, S0, C1, S1). The constructed scheme is detailed in Fig. 1.
Figure 1: Proposed Kyber.PAKE Scheme.
Let’s clarify the design step of the proposed Kyber.PAKE for each sub-processes.
-
Phase C0: The key pairs (pk, sk) are computed according to Kyber’s MLWE-based key generation procedures with the help of KYBER.CCAKEM.KeyGen() and KYBER.CPAPKE.KeyGen() functions, defined in Table 2. After the computation of raw pk, the client generates and sends the encapsulated pk (m = pk + γC).
-
Phase S0: On the server side, there is no public key computation like client side and the server retrieves raw pk (pk = m + γS) using the password-related term. The key component of the server (K) is determined with the usage of the encapsulation procedure of Kyber. The server computes (ct, K) =Kyber.CCAKEM.Enc(pk) and sends K to provide authentication check in the client side.
-
Phase C1: The client retrieves sent values by using decode function and solves the K′′ with help of Kyber’s decapsulation K′′ =Kyber.CCAKEM.Dec(ct, sk), where K is equal to K′′. By making authentication checks, the final password-authenticated shared key is generated.
-
Phase S1: The server makes comparision to ensure the authentication and generates ssk2 = H3(cid||sid||m||γS||pk||K)ΥS0.
In the proposed PAKE, Compress, and Decompress functions, defined in Definition 2, are used to solve the reconciliation problem as a part of Kyber.CCAKEM.Enc and Kyber.CCAKEM.Dec procedures and K = K′′ equality is obtained.
Let’s deeply analyze the relationship between these two terms to show which conditions the proposed scheme will run correctly.
-
In Fig. 1, if K = K′′ is satisfied for (ct, K) =Kyber.CCAKEM.Enc(pk) and K′′ =Kyber.CCAKEM.Dec(ct, sk), the correctness of Kyber.PAKE is also captured.
-
In the Kyber.PAKE, pk is retrieved by using the password component. In the S0 phase, if pk = m + γS is correctly solved with the help of m, there is no changes on the correctness of Kyber.
-
Let’s prove the correctness of Kyber.PAKE based on Theorems 1 and 2.
Let Kyber KEM be correct with (1 − δ) probability (Bos et al., 2018). Then, Kyber.PAKE scheme will also run correctly with (1 − δ) probability.
According to the detailed definition of and Kyber.CCAKEM.Enc in Bos et al. (2018), it uses Kyber.CPAPKE.Enc procedure to generate (ct, K), where ct = (u, v). In Fig. 1, the input of Kyber.CCAKEM.Enc is pk and computed with pk = m + γS. Since if the server correctly recover the m from pk with pk = m + γS = pk + γC + γS, where γC = − γS. By rewriting Remark 1 in Bos et al. (2018), Eq. (4) is obtained. (4) Since there is no component to change the idea of Remark 1 in Bos et al. (2018), if , then the correctness of Kyber.PAKE is satisfied with (1 − δ) probability.
Security Analysis
In the security analysis, MLWE-based PAK components are used to show that A’s probability of obtaining information about the session key with an online dictionary attack is negligible. In the adapted security model, A can make the following client-action (CA) and server-action (SA) queries.
-
CA0: A does CA0 action to instruct the unused instance to transfer the related components to S.
-
SA1: A does SA1 action to transfer the messages to unused instance.
-
CA1: A does CA1 action to transfer the related message to instance that waits the related components of the scheme.
-
SA2: A does SA2 action to transfer the messages to unused instance that waits the final components of the scheme.
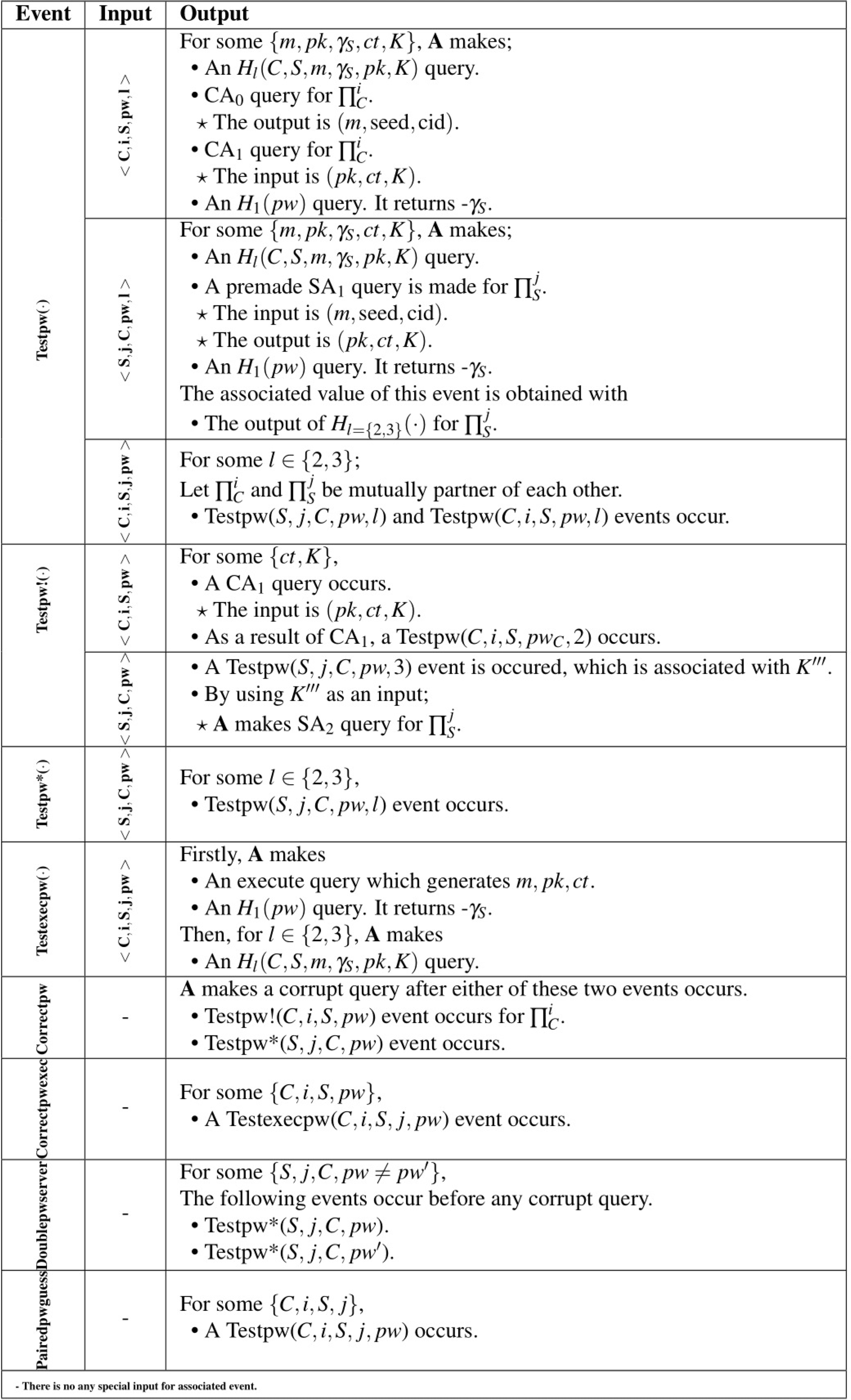
According to the MLWE-based PAKE security analysis, A can take on the role a , a , and partner instances by using the some actions and special events. In the examinations, we modified the password guess events regarding MLWE and Kyber structures and presented them in Table 3 as the constructed Kyber.PAKE relies on the hardness assumption of MLWE and uses the Kyber components.
The Kyber.PAKE’s proof of security is conducted by showing that A is unable to obtain the new ssk with a non-negligible advantage than the online dictionary attack. The advantage of A is given in Theorem 3.
Let the proposed Kyber.PAKE scheme inFig. 1be represented by S, the password dictionary’s size be presented with DS, , and the running time of A be T. For T′ = O(T + (no + ns + ne)Texp), the advantage of A over the Kyber.PAKE scheme is given inEq. (5).
Following PAK security analysis (MacKenzie, 2002), schemes {S = S0, S1, …, S6} are used to prove Theorem 3. In each scheme, A gains a different feature to make an online dictionary attack. Finally, he/she can create a password guess in the S6. The security of the proposed scheme is examined by proving that the advantage of A obtaining the session key of a fresh instance will be smaller than an online dictionary attack.
S0: It is the original Kyber.PAKE scheme.
S1: Let m or pk be chosen randomly by honest participants. If these values already appeared in the previous schemes, S1 halts and A fails.
Let .
For any A,
Let’s define E1 and E2 to describe the random selection of m and pk. For E = E1⋁E2, if the event E occurs, then S1 is equal to S0.
-
Let E1 be an event defined for m = m1 = m2 = m3 = m4 in the following cases.
-
By making CA0 or execute, m1 is obtained.
-
m2 is generated by a previous CA0 or execute.
-
m3 is used as an input of previous SA1.
-
m4 is utilized in a previous query Hl∈{2,3}(⋅).
-
-
Let E2 be an event determined for pk = pk1 = pk2 = pk3 = pk4 in the following cases.
-
By making SA1 or execute, pk1 is generated.
-
pk2 is obtained by a previous SA1 or execute.
-
pk3 is utilized as an input of previous CA1.
-
pk4 is used in a previous query Hl∈{2,3}(⋅).
-
Considering the events E1 and E2, it is necessary to examine whether m and pk are previously or newly generated. In these events, the actions CA 0 and SA 1 are related to send and Hl∈{2,3}(⋅) queries are associated with RO queries. The previously generated m or pk can be obtained by making send, execute, and RO queries. So, the probability of m or pk occurring in the previous session is . Since new m or pk can be generated with send and execute, the maximum number of queries is (ne + ns). Therefore, the probability that E happens is .
S2: Unlike S1, send and execute are replied without answering any RO queries. Afterward, if the RO query is made, the answers are generated as consistently as possible with send and execute. The possible queries and answers in S2 are given in Algorithm 1 .
Let .
For any A ,
In S2, since m and pk are new due to S1, Hl∈{2,3}(⋅) is also new. Therefore, the main condition for distinguishing S1 and S2 is that A queries Hl(⋅) for l ∈ {2, 3}. In Algorithm 1 , there are two possible cases.
-
Since A does not make any H1(pwC), where −γS = H1(pwC), the maximum number of Hl(⋅) queries A can make is .
-
A makes send(C, i, K′) or send(S, j, K′′′) queries using the actions CA0, CA1, SA1, and SA2 in Algorithm 1 . Neither of these queries is the output of an H2(⋅) query that would be a correct password guess. Therefore, the maximum probability that A can abort the samples is .
So, Claim 3 is satisfied.
S3: Unlike S2, the consistency is not controlled against the query execute when an Hl∈{2,3} is queried. In other words, the event Textexecpw(C, i, S, j, pwC) is not checked. So, the scheme responds with a random output rather than maintaining consistency with the query execute. Let , where T′ = O(T + (no + ns + ne)Texp).
For any A,
Let E3 be the occurrence of the event Correctpwexec in S3. If E3 happens, S2 and S3 are distinguishable. In Table 3, if Correctpwexec occurs, the event Testexecpw(C, i, S, j, pw) occurs with two consequences. Given (A, α, φ, ct),
-
In the query execute, m = α + (As1 + e1) and pk = φ + m + γS is set, where and e1←rβq. Then, ct←rDct is chosen.
-
Then, A makes query Hl∈{2,3}(⋅), where m and pk were obtained by query execute. With query H1(pwC), −γS = Ash + eh is determined, where and eh←rβq. Under these changes, the simulator computes (ct′, K′) = Kyber.CCAKEM.Enc(pk). Then, the obtained (ct′, K′) is added on the possible values’s list.
Since the advantage of A in Kyber KEM, given in Definition 4, is and the probability of d-MLWE being resolved is , Claim 3 is satisfied.
S4: Unlike S3, S4 halts when a correct password guess is made against a or instance before any query corrupt. In other words, the event Correctpw happens. Then, A automatically succeeds.
For any A,
If the event Correctpw occurs,
-
In an action CA1 to , if corrupt is not queried after Testpw!(C, i, S, pwC), S4 halts and A succeeds.
-
In a query Hl∈{2,3}(⋅), if corrupt is not queried after Testpw*(S, j, C, pwC), S4 halts and A succeeds.
Claim 5 is satisfied as these changes will only increase the win probability of A.
S5: Unlike S4, S5 halts when A guesses a password against the partner instances and . In other words, the event Pairedpwguess happens. Then, A fails.
For any A,
For some {C, i, S, j}, if Pairedpwguess occurs, a Testpw(C, i, S, j, pwC) also occurs. In this event, there is a partnership between and . Let d←r{1, 2, …, ns} be chosen and (A, α, φ, ct) is given. In S5, Algorithm 2 changes are simulated by A.
Since the ROM security of Kyber KEM, given in Definition 4, is and the probability of d-MLWE being solved with send queries is , Claim 5 is satisfied.
_______________________
Algorithm 1 S2 Queries and Answers____________________________________________________
⋅ In an execute(C,i,S,j) query, m = As + e, where s ←r bkη and ei ←r bη,
pk ←r Dpk, ct ←r Dct, {K,K′′′} ←r {0,1}k, and {sskj
2 = sski
1} ←r
{0,1}k.
⋅ In a CA0 action to ∏i
C, m = As + e, where s ←r bk
η and ei ←r b
η.
⋅ In a SA1 action to ∏j
S, pk ←r D
pk, ct ←r D
ct, K ←r {0,1}k, and
{K′,sskj
2}←r {0,1}k.
⋅ In a CA1 action to ∏i
C:
– As a result of this query, if a Testpw!(C,i,S,pwC) happens, then K′′′
and sski1 are set to the associated value of Testpw(C,i,S,pwC,2) and
Testpw(C,i,S,pwC,3).
– If ∏i
C has a partner ∏j
S, sskj
2 = sski
1. Then, K′′′ ←r {0,1}k.
– If not, ∏i
C aborts.
⋅ As a result of an SA2 action, if one of the following conditions is satisfied,
it terminates. If not, ∏j
S aborts.
– If an Testpw!(S,j,C,pwC) happens, or ∏j
S has a partner ∏i
C.
⋅ As a result of an Hl∈{2,3}(C,S,m,γS,pk,K), if one of the following condi-
tions is met, the output is determined by considering the associated value
of the event. If not, the output is randomly chosen from {0,1}k.
– If a Testpw(S,j,C,pwC,l) or a Testexecpw(C,i,S,j,pwC) happens._
_______________________________________________________________________________________________________
Algorithm 2 S5 Changes_____________________________________________________________________
⋅ For the d-th send(C,i′,S) query to ∏i′
C, m = α is set.
⋅ In a send(S,j,< C,m,seed >), pk = φ + m + γS is computed.
⋅ In a send(C,i′,< pk,ct,K >), if there is no partner for ∏i′
C, the output is
0 and S5 halts.
⋅ Let ∏j
S and ∏i′
C be partner after its send(S,j,< C,m,seed >) in a
send(S,j,K′) query to ∏j
S. If the instances have no partnership after
this query and Correctpw is not tested, ∏j
S aborts.
⋅ Then, A makes Hl∈{2,3}(⋅) query, where m and pk were obtained with ∏i′
C.
The output of H1(pwC) query is defined by −γS = Ash +eh, where sh ←r
bkη and eh ←r bη. Under these changes, the simulator computes (ct′,K′) =
Kyber.CCAKEM.Enc(pk). Then, the obtained (ct′,K′) is added to the
possible values list._______________________________________________________________________ S6: Unlike S5, in S6, there is an internal password oracle that can know all passwords for a given client/server pair and test the correctness of the provided password.
For any A,
Using the password oracle,
-
All passwords are generated during initialization and special passwords can be tested in the following way. If pw = pwC, the output of testpw(C, pw) is True. Otherwise, the output is False.
-
All corrupt(U) is accepted and answered.
In S6, Testpw(C, i, S, pw) for , Testpw(S, j, C, pw) for , and Testpw(C, pw) for password oracle queries are checked whether Correctpw occurs. So, S5 and S6 can be completely indistinguishable. Claim 6 is satisfied.
In S6, A has two ways to gain a non-negligible advantage against Kyber.PAKE.
-
Online dictionary attack: CDF-Zipf model, given in Definition 8, limits the probability of Correctpw event in the proposed Kyber.PAKE since Correctpw event is A’s successful obtaining of the password through online dictionary attacks. In other words, .
-
A test query: Let be a fresh instance. Then, A makes a query test(U, i) to . Since the view of A is completely independent of , .
By considering these two options, Eq. (6) is obtained. (6)
According to Eq. (2), . If Eq. (2) is rewritten by considering Claims (2)–(7), Eq. (7) is obtained. (7) Since , Theorem 3 is hold.
Reference Implementation and Comparison Results
In this section, the reference implementation of Kyber.PAKE is presented in terms of cost, CPU cycle, running time, and memory usage. In addition, detailed comparisons with literature proposals based on performance evaluations are also provided.
The implementation of Kyber.PAKE is written in C (Dursun, 2023a) based on Kyber KEM’s reference C codes and PAK design components. The performance results are obtained by using a computer with a 2.5 GHz dual-core Intel Core i5 processor and 8 GB RAM. The obtained performance evaluation is compared with MLWE.PAKE scheme (Ren, Gu & Wang, 2023) since it is the only MLWE-based PAKE in the literature. For these two schemes, the parameter sets are recalled in Table 4.
| Scheme | Security level | k | n | q | η | η1 | η2 | (du, dv) | δ |
|---|---|---|---|---|---|---|---|---|---|
| MLWE.PAKE (Ren, Gu & Wang, 2023) | 116 | 2 | 256 | 7,681 | 13 | x | x | x | 2−53.4 |
| 177 | 3 | 256 | 7,681 | 8 | x | x | x | 2−97.4 | |
| 239 | 4 | 256 | 7,681 | 6 | x | x | x | 2−131.6 | |
| Proposed Kyber.PAKE | 128 | 2 | 256 | 3,329 | x | 3 | 2 | (10,4) | 2−131 |
| 192 | 3 | 256 | 3,329 | x | 2 | 2 | (10,4) | 2−164 | |
| 256 | 4 | 256 | 3,329 | x | 2 | 2 | (11,5) | 2−174 |
To obtain comparisons in terms of running time, MLWE.PAKE and our implementation are run 1,000 times. Based on the main processes or functions, the CPU cycles are determined for 128-bit security level and presented in Table 5. It can be seen from Table 5, the proposed Kyber.PAKE scheme needs fewer average and media CPU cycles due to the small size of the parameter set and its efficient/simple structure components.
| MLWE.PAKE (Ren, Gu & Wang, 2023) | Kyber.PAKE | |||
|---|---|---|---|---|
| Functions/Processes | Avg. | Med. | Avg. | Med. |
| GenMatrix() | 31,108 | 27,997 | 24,188 | 22,109 |
| PolyGetNoise() | 4,412 | 4,112 | 3,943 | 3,512 |
| PolyNtt() | 13,429 | 12,664 | 7,798 | 7,443 |
| PolyvecNtt() | 33,170 | 27,061 | 15,024 | 14,121 |
| PolyvecInvntt() | 30,621 | 26,460 | 21,248 | 19,906 |
| OkcnCon() | 17,699 | 16,058 | x | x |
| OkcnRec() | 3,489 | 3,297 | x | x |
| Kyber.CCAKEM.Enc() | x | x | 182,018 | 165,958 |
| Kyber.CCAKEM.Dec() | x | x | 193,497 | 173,239 |
| C0 | 195,201 | 173,157 | 143 497 | 124 864 |
| S0 | 307,547 | 265,276 | 224,537 | 183,024 |
| C1 | 133,436 | 117,676 | 256,217 | 228,652 |
| S1 | 40,446 | 30,603 | 59,907 | 57,807 |
Notes:
Bold values indicate cases where the proposed scheme provides better results than the compared ones in terms of the analyzed metrics.
Table 6 gives the average run time results, which is constructed by considering common components, scheme phases, hash functions, and reconciliation structures. Due to its parameter set, Kyber.PAKE provides better results in generating pk (A) with GenMatrix() and hash functions. Since KEM structures such as encapsulation and decapsulation, which have additional components for security, are used in Kyber.PAKE, it requires more runtime than MLWE.PAKE in terms of reconciliation. Considering the total times on the client and server sides, MLWE.PAKE is better on the client side. One of the reasons is that in MLWE.PAKE, key generation takes place on both the client and server sides, while it is only made on the client side of Kyber.PAKE. Different design approaches, reconciliation functions, and parameter sets also affect.
| Scheme security level | (Ren, Gu & Wang, 2023) 116 | Kyber.PAKE 128 | (Ren, Gu & Wang, 2023) 177 | Kyber.PAKE 192 | (Ren, Gu & Wang, 2023) 239 | Kyber.PAKE 256 |
|---|---|---|---|---|---|---|
| GenMatrix() | 13.893 | 9.256 | 27.504 | 21.648 | 49.979 | 38.713 |
| OkcnCon() | 7.058 | x | 5.920 | x | 5.293 | x |
| OkcnRec() | 1.425 | x | 1.622 | x | 1.655 | x |
| Kyber.CCAKEM.Enc() | x | 69.133 | x | 110.894 | x | 152.360 |
| Kyber.CCAKEM.Dec() | x | 72.362 | x | 117.631 | x | 177.787 |
| shake128 | 2.656 | 2.390 | 2.422 | 2.923 | 3.036 | 2.397 |
| shake256 | 13.386 | 11.328 | 16.680 | 16.235 | 22.904 | 21.586 |
| C0 | 87.456 | 52.449 | 112.925 | 88.894 | 155.515 | 141.205 |
| S0 | 126.205 | 71.135 | 155.530 | 114.015 | 202.895 | 165.042 |
| C1 | 50.409 | 93.443 | 70.565 | 150.637 | 90.342 | 217.362 |
| S1 | 12.942 | 21.781 | 16.689 | 32.918 | 21.930 | 42.184 |
| Total client | 138.865 | 145.892 | 183.490 | 239.531 | 245.857 | 358.567 |
| Total server | 139.147 | 92.916 | 172.219 | 146.993 | 224.825 | 207.256 |
Notes:
Bold values indicate cases where the proposed scheme provides better results than the compared ones in terms of the analyzed metrics.
The computational cost evaluation of lattice-based two-party PAKEs that were constructed by following the one-phase idea is also provided with Table 7. Even if the selected schemes were designed under the same approach, the main securities were captured with different hard problems. So, message size-based evaluation is just presented in Table 7.
| Reference | Hardness | Security level | C | S | C+S |
|---|---|---|---|---|---|
| Gao et al. (2017) | RLWE | 82 | 3,904 | 4,000 | 7,904 |
| Ding et al. (2017) | RLWE | 76 | 4,136 | 4,256 | 8,392 |
| Yang et al. (2019) | RLWE | 206 | 1,864 | 2,592 | 4,456 |
| Ren, Gu & Wang (2023) | 116 | 928 | 1,056 | 1,984 | |
| MLWE | 177 | 1,344 | 1,472 | 2,816 | |
| 239 | 1,760 | 1,888 | 3,648 | ||
| Kyber.PAKE | 128 | 864 | 1,568 | 2,432 | |
| MLWE | 192 | 1,248 | 2,272 | 3,520 | |
| 256 | 1,632 | 3,136 | 4,768 |
Notes:
Bold values indicate cases where the proposed scheme provides better results than the compared ones in terms of the analyzed metrics.
In Table 7, the provided results are obtained in the following way. It can be seen in Kyber.PAKE’s protocol flow, {seed, cid, mbytes, K′′′} are transferred to the server. On the server side, {pk, ct, K} components are sent to the client. According to the selection or computations of these values, it is known that {seed, cid, K, K′′′} are fixed 32-byte and {mbytes, pkbytes} = k⋅384, where k is determined differently for each security levels.
Let’s show how the message sizes of Kyber.PAKE is computed for 128 −bit security level.
-
Client to Server: seed + cid + mbytes + K′′′ = 32 + 32 + (2⋅384) + 32 = 864 bytes.
-
Server to Client: pkbytes + ctbytes + K = (2⋅384) + 768 + 32 = 1,568 bytes.
The comparisons inTables 5 and6 are conducted by assuming that (Ren, Gu & Wang, 2023) presents approximately the same security levels. Note that Kyber.PAKE will provide better results when the parameters are changed to achieve the same security levels.
Using the Kyber.PAKE C codes (Dursun, 2023a), Java codes (Dursun, 2023b) are also written to demonstrate the usability of the proposed scheme on mobile devices. In the implementation, a computer with a 2.5 GHz dual-core Intel Core i5 processor and 8 GB RAM is used as the server. Samsung Galaxy A51 (8 Cores) with 4x 2.3 GHz ARM Cortex-A73 main processor and 4x 1.7 GHz ARM Cortex-A53 co-processor with 2.3 GHz CPU frequency device is utilized as the client. Kyber.PAKE mobile results in terms of runtime, memory, and CPU usage are given in Table 8, which is obtained by running all the phases of the client and server 1,000 times.
| Security level | Phase | Running time* | Memory usage | CPU usage |
|---|---|---|---|---|
| C0 | 745.918 | 104.2 KB | %8 | |
| S0 | 880.761 | 88.6 KB | %10 | |
| 128 | C1 | 997.569 | 168.3 KB | %10 |
| S1 | 446.311 | 0.4 KB | %7 | |
| Total client | 1743.487 | 272.5 KB | %18 | |
| Total server | 1327.072 | 89 KB | %17 | |
| C0 | 918.225 | 148.2 KB | %10 | |
| S0 | 945.361 | 133.7 KB | %11 | |
| 192 | C1 | 1215.136 | 211.4 KB | %12 |
| S1 | 611.217 | 0.4 KB | %8 | |
| Total client | 2133.361 | 359.6 KB | %22 | |
| Total server | 1556.578 | 134.1KB | %19 | |
| C0 | 1211.843 | 177.8 KB | %11 | |
| S0 | 1388.745 | 171.1 KB | %13 | |
| 256 | C1 | 1811.257 | 297.2 KB | %14 |
| S1 | 874.413 | 0.5 KB | %10 | |
| Total client | 3023.1 | 475 KB | %25 | |
| Total server | 2236.158 | 171.6 KB | %23 |
Notes:
Bold values indicate cases where the proposed scheme provides better results than the compared ones in terms of the analyzed metrics.
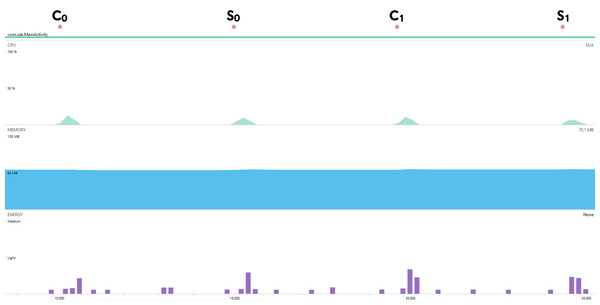
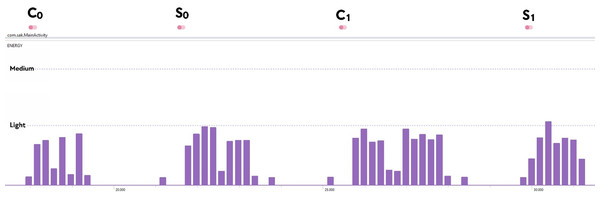
The mobile device compatibility of Kyber.PAKE is also analyzed regarding energy, memory, and CPU usage. For 128-bit security, each sub-processes of Kyber.PAKE is examined with the Android Profiler tool of Android Studio and given in Fig. 2. As a case scenario, the energy consumption metric is also detailed in Fig. 3.
Figure 2: Energy, memory, and CPU usages for mobile Kyber.PAKE
Figure 3: Energy Consumption of Mobile Kyber.PAKE.
Figures 2 and 3 show that although the proposed PAKE does not contain any optimization or improvement techniques, it has relatively low resource usage. So, we can say that constructed Kyber.PAKE will be preferred to obtain the post-quantum secure mobile environment.
Note that two other lattice-based PAKE schemes (Dabra, Bala & Kumari, 2020; Ding, Cheng & Qin, 2022; Seyhan & Akleylek, 2024) for two-party mobile device security were proposed using different approaches, hardness, and additional properties. When we checked the proposals, no source code was given, and the results were not provided for all metrics, such as memory, CPU, and energy usage. Therefore, we compared MLWE-based PAKEs in terms of running times and presented a computational cost examination for all two-party PAK PAKEs.
Conclusion and Future Directions
In this article, a two-party PAKE version of Kyber KEM is constructed to provide a proposal for post-quantum PAKE requirements by adapting the standard algorithms for different purposes and usage areas. Kyber.PAKE is obtained by adjusting the traditional PAK design idea to the MLWE problem and Kyber KEM functions. In the password-authenticated shared key generation, it is shown that explicit authentication and PFS properties are captured. The security of Kyber.PAKE is analyzed by considering dictionary attack resistance under the ROM assumptions. In these examinations, the CDF-Zipf model is also added to determine more realistic security proofs by considering the real-world distribution of the passwords. The reference implementation results show that the Kyber.PAKE scheme can be one of the best choices in post-quantum era security in terms of run-time, memory, and CPU usage. The mobile device usage of the proposed PAKE is also analyzed by providing reference Java implementation. As far as we know, the constructed Kyber.PAKE is the first PAKE adaptation of the NIST PQC KEM standard with mobile environment compatibility. As a future direction, the security examination of Kyber.PAKE will be extended by defining quantum random oracle model assumptions and the resource-limited device usage will be provided by making arithmetic optimizations and improvements.